I analysed a random piece of malware from MalwareBazaar. {Static Analysis}

Today, I decided to analyse a random piece of malware from MalwareBazaar. To begin, I set up a virtual machine using FlareVM. I ensured network connectivity was disabled and took a pre-execution snapshot so I could safely revert the system if needed.

My next step was to select a malware sample from MalwareBazaar.

My initial appreciation for FlareVM came from how clearly it shows whether you're connected to the internet. As with most samples from MalwareBazaar, this one was delivered in a password-protected ZIP archive. After extracting the executable, I began a basic static analysis.
File Hashes:
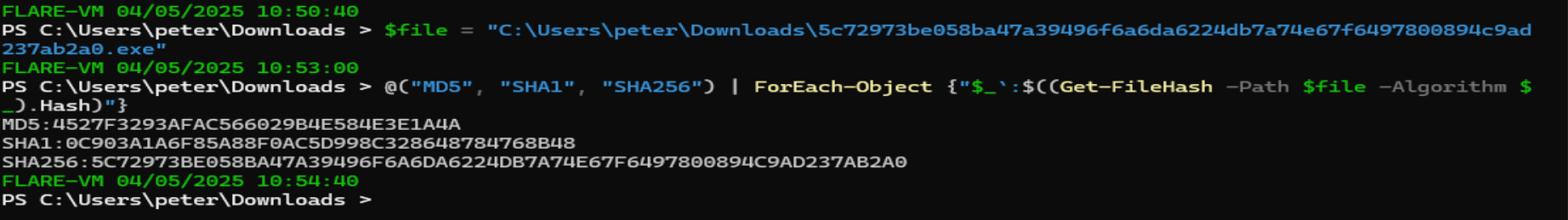
- SHA256:
5c72973be058ba47a39496f6a6da6224db7a74e67f6497800894c9ad237ab2a0 - SHA1:
0c903a1a6f85a88f0ac5d998c328648784768b48 - MD5:
4527f3293afac566029b4e584e3e1a4a
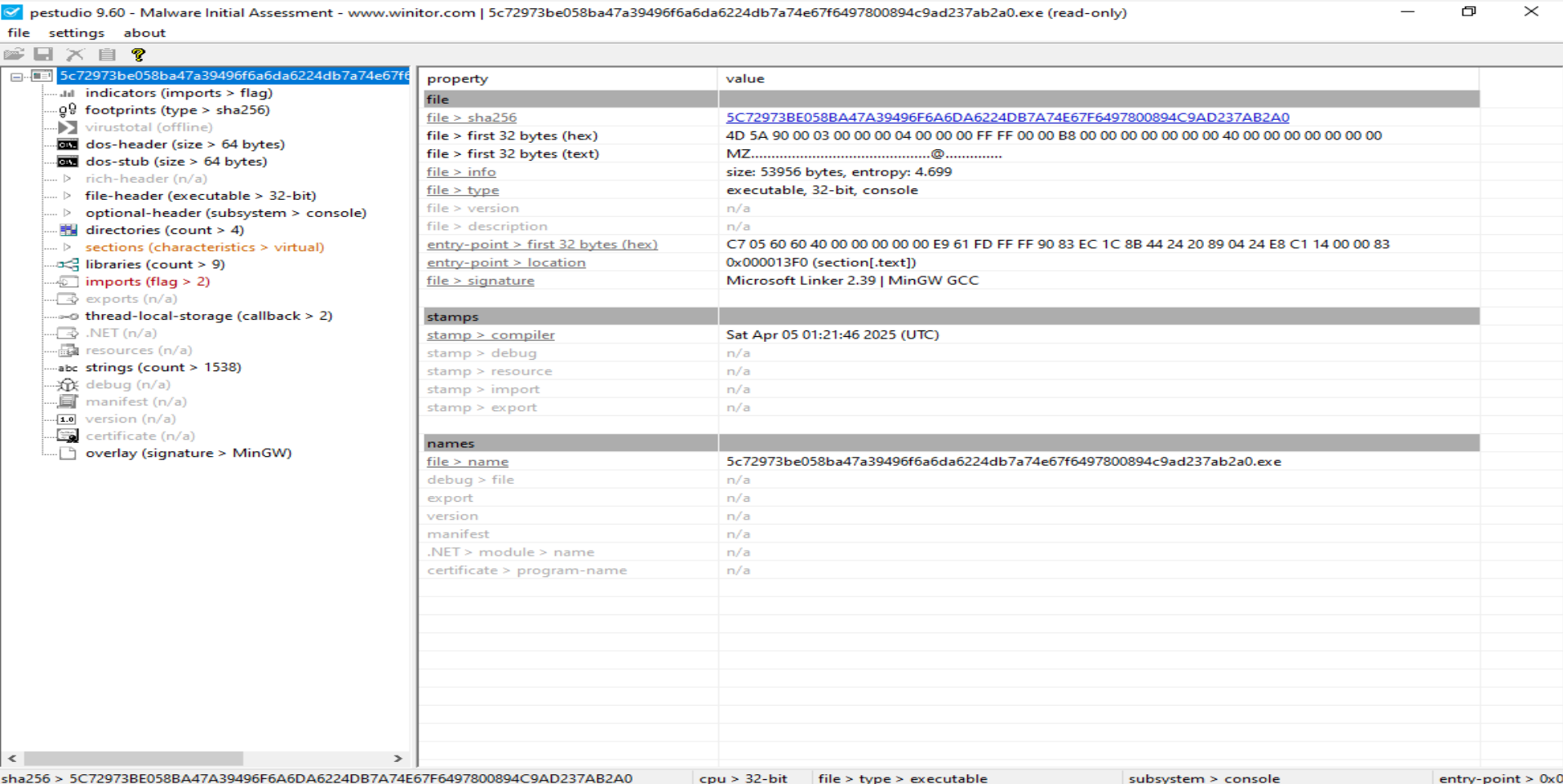
Querying the SHA256 hash on VirusTotal revealed that the original file name was prog.exe, with a file size of 52.69 KB (53956 bytes). It's identified as a Win32 EXE.
Timeline (based on VirusTotal):
- Creation Time: 2025-04-05 01:21:46 UTC
- First Submission: 2025-04-05 04:46:14 UTC
- Last Submission: 2025-04-05 08:33:39 UTC
- Last Analysis: 2025-04-05 07:36:31 UTC
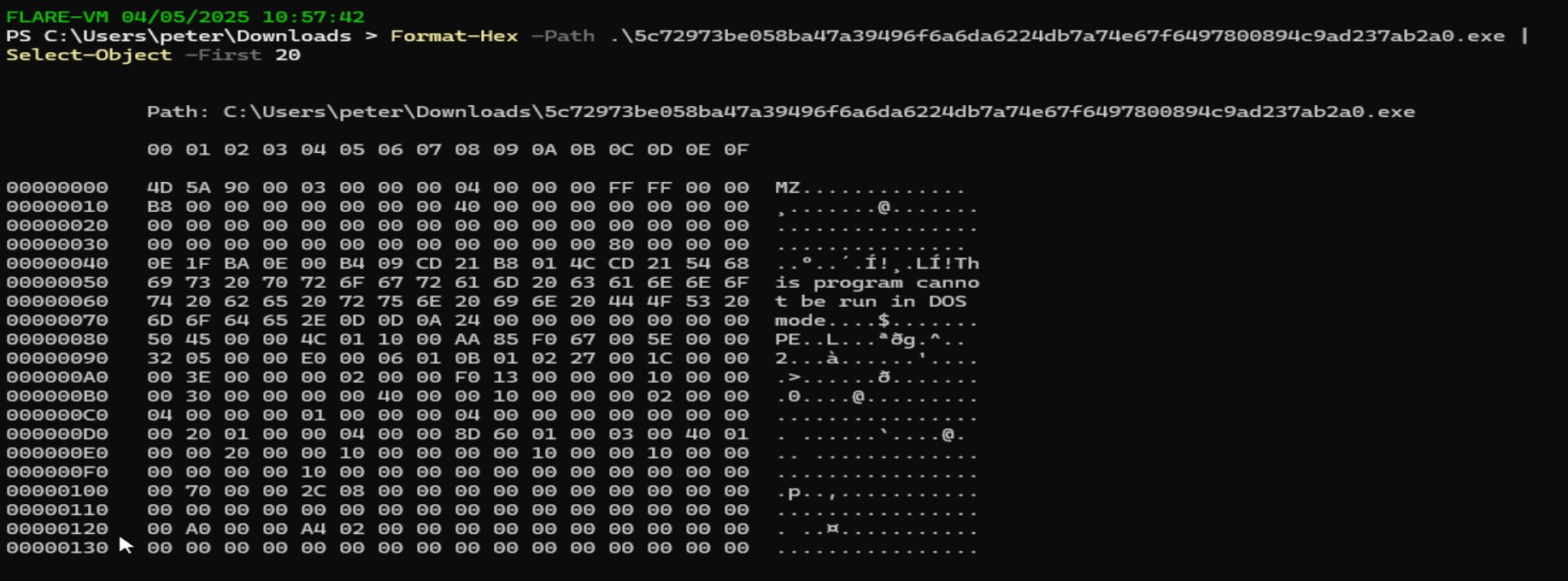
File Structure and Entropy
Inspecting the file's hex reveals the familiar DOS MZ header, confirming it's a Windows executable. The presence of the value 0xFFFF indicates that the file cannot run in DOS mode—again, consistent with a Windows-only executable. This is also supported by the side message within the header.
The file’s entropy is calculated at 4.699, which isn't immediately suspicious. However, the presence of an overlay with an entropy of 3.844 is worth noting. Overlays can sometimes be used to conceal additional data or code.
Indicators and Imports
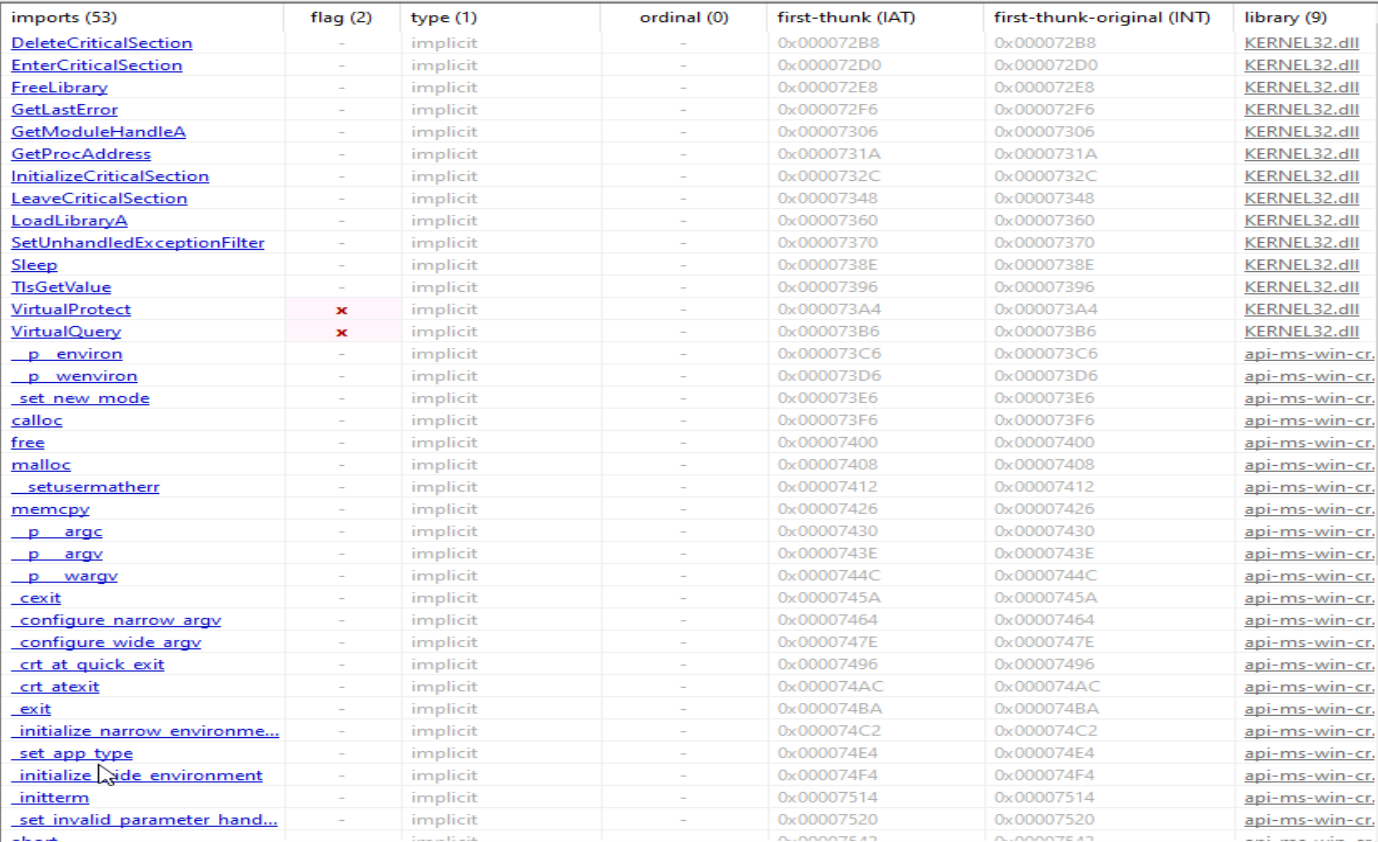
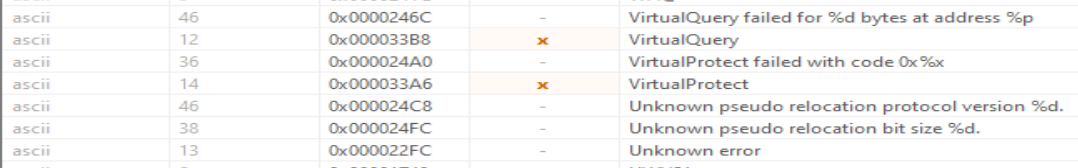
VirusTotal assigned the tag checks-user-input, which matches some of the imported functions observed during analysis.
Keyloggers often make use of:
- Threading (e.g.,
EnterCriticalSection,LeaveCriticalSection) - Dynamic function resolution (
GetProcAddress) - Memory operations (
VirtualProtect,VirtualQuery)
Interestingly, this sample does not import SetWindowsHookEx, which is traditionally associated with keylogging. Instead, it imports TlsGetValue. In the context of an info-stealer, this is notable—TlsGetValue can be used to retrieve input data from thread-local storage (TLS) slots. This allows the malware to bypass standard keyboard hooks and potentially extract session data from applications like browsers. This method extends beyond simple keylogging, as it may enable access to previously stored credentials.
Interesting Strings
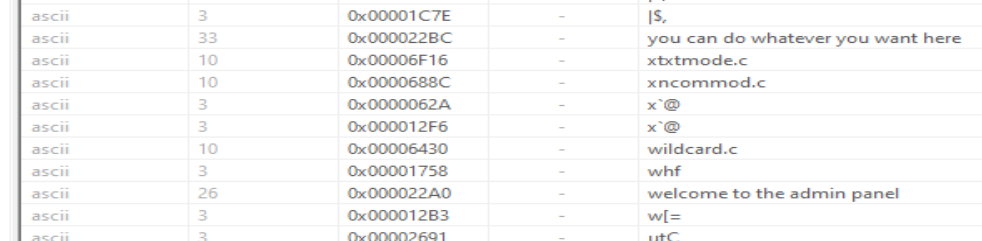
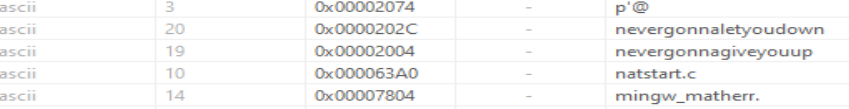
Reviewing the sample’s embedded strings revealed some noteworthy elements:
- "you can do whatever you want here" and "welcome to the admin panel"
These suggest an admin interface might exist, potentially for controlling or configuring the malware. - Lyrics from Rick Astley’s "Never Gonna Give You Up"
This could be a reference or possibly used for obfuscation—e.g., as part of an encryption/decryption routine or even as an authentication string for a C2 server. - Credential prompts
These may be dummy prompts designed to harvest user credentials or serve as authentication prompts for accessing malware functionality or its admin panel. - "fake" values
These could be part of an anti-analysis technique—introducing misleading or irrelevant data to waste analysts’ time or reduce entropy flags. - Debug/logging strings
These may support internal error handling, possibly useful for malware development or real-time feedback during execution.

Observed Network Activity
VirusTotal provided a list of IP addresses associated with the malware's network activity:
- TCP 20.99.133.109:443
- TCP 184.27.218.92:80
- TCP 20.96.153.111:443
- TCP 23.196.145.221:80
- TCP 23.46.228.139:443 (res.public.onecdn.static.microsoft)
- TCP 23.96.180.189:443
- TCP 23.32.75.19:80
Using my own SOC OSINT Extension (available on the Firefox Extension Store and soon on Chrome), I reviewed these IPs on AbuseIPDB. The most recent was last flagged around two months ago, suggesting they may still be active or have been reused.
Below is a table summarising key static analysis findings:
| Filename | prog.exe |
| Hash Values | |
| SHA256 | 5c72973be058ba47a39496f6a6da6224db7a74e67f6497800894c9ad237ab2a0 |
| SHA1 | 0c903a1a6f85a88f0ac5d998c328648784768b48 |
| MD5 | 4527f3293afac566029b4e584e3e1a4a |
| File type | Win32 EXE |
| File size | 52.69KB |
| File Entropy | 4.699 |
| Overlay Entropy | 3.844 |
| Creation Time | 2025-04-05 01:21:46 UTC |
| First Submission | 2025-04-05 04:46:14 UTC |
| Notable Imports | |
| GetProcAddress | |
| GetModuleHandleA | |
| InitializeCriticalSection | |
| LeaveCriticalSection | |
| TlsGetValue | |
| DeleteCriticalSection | |
| EnterCriticalSection | |
| FreeLibrary | |
| GetLastError | |
| VirtualProtect | |
| VirtualQuery | |
| Notable Strings | |
| welcome to the admin panel | |
| nevergonnaletyoudown | |
| nevergonnagiveyouup | |
| hey there! what's the username: | |
| hey there! what's the password: | |
| fake | |
| VirtualQuery failed for %d bytes at address %p | |
| Network Communications | |
| TCP 20.99.133.109:443 | |
| TCP 184.27.218.92:80 | |
| TCP 20.96.153.111:443 | |
| TCP 23.196.145.221:80 | |
| TCP 23.46.228.139:443 (res.public.onecdn.static.microsoft) | |
| TCP 23.96.180.189:443 | |
| TCP 23.32.75.19:80 |